HTTPS ensures that communication between the client and server is encrypted, so that if it is intercepted, the third party cannot easily view or use the information. For FME Server, you can use HTTPS to ensure that sensitive log in information is not exposed. This is especially important if you are using the Active Directory integration.
Enabling FME Server SSL Support
To enable SSL support:
- Modifying Service URLs to Use HTTPS
- Enable SSL on the Web and/or Application Server
- Enable SSL on the WebSocket Server
- Verify the Configuration
Modifying Service URLs to Use HTTPS
To enable SSL for a service, open the FME Server Web User Interface, select Manage > Administration > Services, and click the desired service in the table.
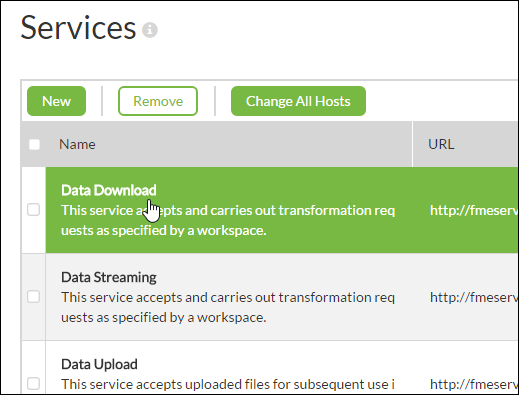
The Editing Service page opens.
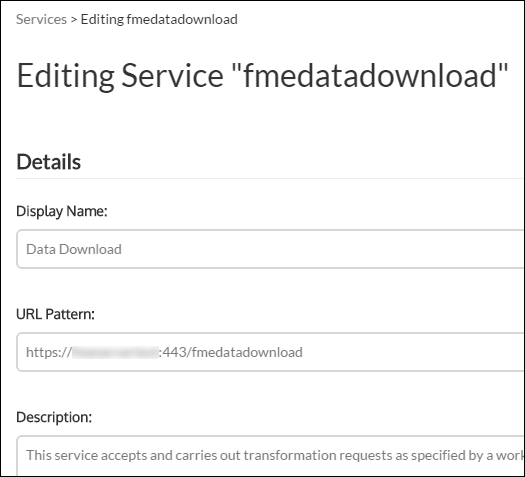
In the URL Pattern field, change HTTP to HTTPS, and modify the port number, if required. Typically SSL is configured on either port 8443 or 443.
Enable SSL on the Web and/or Application Server
Depending on the method, instructions to set up SSL on different application servers vary. The following example provides steps for setting up SSL for Apache Tomcat 7, which is the application server included with an express installation of FME Server.
For any HTTPS (SSL) page, a certificate is required. For development and testing purposes, self-signed certificates are supported. For production use, we recommend that you use SSL certificates from a verified SSL certificate authority (CA).
First, you must generate a keystore that contains a certificate chain using the keytool command from the Java Developer Kit (JDK).
Note: To ensure the security of the keystore file, allow access to it only by users who run the FME Server Services, and select users with administrative privileges on FME Server.
- Open the command prompt.
-
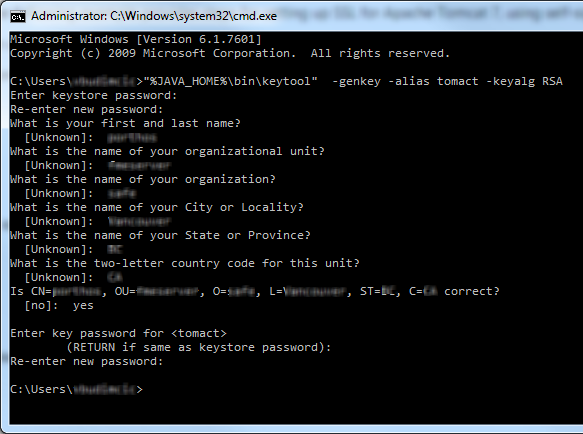
Type the following command:
keytool -genkey -alias tomcat -keyalg RSA
-keystore <your_keystore_filename>
If your path is not set to the Java bin directory, navigate to that directory and type the appropriate command.
Note: A JDK must be installed to use the keytool command.
A message prompts you to enter a keystore password.
-
Enter a password for the keystore.
-
Enter the required details, shown here:
Note: (CA-issued certificates only): Answer "What is your first and last name?" with the server domain name; for example, "fmeserver.example.org".
-
Enter the same password you entered in step 3.
A keystore is generated in the following location:
<drive>:\Users\<username>\.keystore
-
(CA-issued certificates only)
-
Generate a certificate signing request (CSR):
-
Submit the CSR (certreq.scr) to your CA to obtain a certificate, according to your CA's instructions.
-
Import the certificate into the keystore. Depending on the web application server, you may also need to import a root certificate (consult your web application or CA's instructions).
keytool -certreq -keyalg RSA -alias tomcat -file certreq.csr
-keystore <your_keystore_filename>
Import root certificate:
keytool -import -alias root -keystore <your_keystore_filename>
-trustcacerts -file <chain_certificate_filename>
Import certificate:
keytool -import -alias tomcat -keystore <your_keystore_filename>
-file <certificate_filename>
-
-
Copy the .keystore file to the Tomcat directory, and then copy the path to the file.
If you are using the default web application included with FME Server, Tomcat is located at:
<FME Server Install DIR>\Utilities\tomcat
-
Open the server.xml file:
<TomcatDir>\conf\server.xml
-
Locate the Connector code block, and replace it with the following:
<Connector protocol="org.apache.coyote.http11.Http11Protocol"
port="443" minSpareThreads="5"
enableLookups="true" disableUploadTimeout="true"
acceptCount="100" maxThreads="200"
scheme="https" secure="true" SSLEnabled="true"
keystoreFile="C:\Program Files\FMEServer\Utilities\tomcat\.keystore"
keystorePass="<your_password>"
clientAuth="false" sslEnabledProtocols="TLSv1,TLSv1.1,TLSv1.2"
ciphers="TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,
TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,
TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256,
TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA,
SSL_RSA_WITH_3DES_EDE_CBC_SHA"URIEncoding="UTF8" />
<Connector port="80" protocol="HTTP/1.1"
redirectPort="443"/>
Note: The sslEnabledProtocols and
ciphersparameters disallow SSL v3 and ciphers that are considered unsafe. However, these modifications break SSL compatibility with Internet Explorer 6, and may cause unexpected behavior with Java Runtime Environment Version 6.0 Update 45 (Java 6u45). For more information, see http://googleonlinesecurity.blogspot.ca/2014/10/this-poodle-bites-exploiting-ssl-30.html.Note: The values for
cipherspecified above are compatible with Java v8, which is included with FME Server 2015.1.2 and later. For FME Server versions earlier than 2015.1.2, specify these ciphers instead, compatible with Java v7:"TLS_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,. Note that these ciphers have a higher strength rating than those provided in previous versions of the FME Server documentation.
TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,
SSL_RSA_WITH_3DES_EDE_CBC_SHA,TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA" - Be sure to set the keystoreFile path to the correct location and the keystorePass to the password you entered in step 3. Also, if you configured the FME Server Service URLs to use a port other than 443, that port number must be corrected in the
portandredirectPortdirectives. -
Change the Listener className line (found near the beginning of the file) to how it is written below:
<Listener className="org.apache.catalina.core.AprLifecycleListener" SSLEngine='off'/>
- Save the server.xml file.
-
Open the web.xml file:
<TomcatDir>\conf\web.xml
- Add the following code block to the end of the file, just before the closing </web-app> tag:
- Save the web.xml file.
- If you are using the default FME Server Application Server, restart that service. Or, if you are using your own Tomcat application, restart that.
-
Open a browser and navigate to https://localhost:<port>. If you used the same port as specified in Step 9,
<port>is443.This should show you the same Tomcat home page, but in a secured format.
- (Self-signed certificates only) On the machine that hosts the FME Server Core, run the following JDK keytool command from the command prompt:
<security-constraint>
<web-resource-collection>
<web-resource-name>HTTPSOnly</web-resource-name>
<url-pattern>/*</url-pattern>
</web-resource-collection>
<user-data-constraint>
<transport-guarantee>CONFIDENTIAL</transport-guarantee>
</user-data-constraint>
</security-constraint>
keytool -import -v -trustcacerts -alias server-alias -keystore "%JAVA_HOME%\jre\lib\security\cacerts" -file <your self-signed certificate> -keypass <key password> -storepass <keystore password>
This command imports the untrusted certificate into the FME Server database and instructs the web application server to make an exception for it.
Enable SSL on the WebSocket Server
The FME Server WebSocket server supports insecure or secure connections. (Only one or the other protocol is currently supported). To enable SSL, edit the fmeWebSocketConfig.txt file in your server installation (<FMEServerDir>\Server).
- Set
WEBSOCKET_SSL_ENABLED=true. - Uncomment the WEBSOCKET_KEYSTORE_FILE_PATH directive and set it to reference the keystore file you generated under Enable SSL on the Web and/or Application Server. For example:
- Specify the same settings for the WEBSOCKET_ENABLE_SSL, WEBSOCKET_KEYSTORE_FILE_PATH, and WEBSOCKET_KEYSTORE_FILE_PASSWORD directives in the following files:
- <FMEServerDir>\Server\config\subscribers\websocket.properties
- <FMEServerDir>\Server\config\publishers\websocket.properties
WEBSOCKET_KEYSTORE_FILE_PATH=/data/fmeserver/Utilities/tomcat/keystore.jks
Enable SSL on the WebSocket Publisher and WebSocket Subscriber
To enable SSL on the Notification Service WebSocket Publisher and WebSocket Subscriber, update the value property of the PROPERTY directive from "ws://localhost:7078/websocket" to "wss://localhost:7078/websocket" in the following files:
- <FMEServerDir>\Resources\publishers\websocket\publisherProperties.xml
- <FMEServerDir>\Resources\subscribers\websocket\subscriberProperties.xml
Verify the Configuration
To verify that HTTPS is configured properly, perform the relevant checks here, including confirmation that the web services are available, and confirmation that FME Server can run a job.
See Also