General
Specifies whether or not the reader should increase the logging verbosity. Possible values are Yes and No. The default is No.
Specifies whether the images files referenced by Overlay elements should be read as raster geometry.
If set to All, all GroundOverlay, PhotoOverlay, and ScreenOverlay images will be read as raster geometry.
If set to GroundOverlay, then only GroundOverlay images will be read.
Specifies whether or not the reader should scan the KML files for schema elements.
If this box is not checked, KML elements will be read using the fixed schema. KML datasets using the KML 2.1 schema may not be read properly unless this option is checked.
Specifies whether or not the reader should terminate the translation if a network error occurs.
Specifies whether or not the reader should delete temporary files downloaded as part of the reading process.
Specifies whether or not NetworkLink or schemaUrl references to external KML files should be traversed (i.e. to read the referenced document).
If Local is specified, then references will only be traversed if they refer to a file on the local filesystem.
If the value of this parameter is 'Yes', the companion '.prj' and '.wld' files (having the same name as the '.obj' file) will be read to acquire the coordinate system and the data necessary to convert points to the world coordinate system.
Note: Note: In the absence of a companion ‘.wld’ file with the same name as the ‘.obj’ file, a file named ‘global.wld’ will be looked for in the same folder. Similarly for the companion ‘.prj’ file, only in that case we will only look for a file named ‘global.prj’.
Specifies whether or not scaling and orientation metadata in the KML Placemark will be applied to the model geometry prior to being output.
Specifies the maximum depth of the traversal tree.
The traversal depth is the number of links that must be traversed to get from the original file to the root file. For example, if the dataset root refers to DocB, which refers to DocC, the traversal depth is 2.
Schema Attributes
Use this parameter to expose Format Attributes in Workbench when you create a workspace:
- In a dynamic scenario, it means these attributes can be passed to the output dataset at runtime.
- In a non-dynamic scenario where you have multiple feature types, it is convenient to expose additional attributes from one parameter. For example, if you have ten feature types and want to expose the same attribute in each one, it is easier to define it once than it is to set each feature type individually in the workspace.
Using the minimum and maximum x and y parameters, define a bounding box that will be used to filter the input features. Only features that intersect with the bounding box are returned.
If all four coordinates of the search envelope are specified as 0, the search envelope will be disabled.
Select this parameter to remove any portions of exported features outside the area of interest.
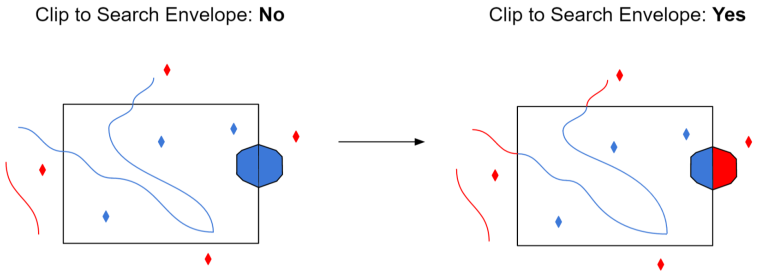
The illustration below shows the results of the Search Envelope when Clip to Search Envelope is set to No on the left side and Yes on the right side.
- No: Any features that cross the search envelope boundary will be read, including the portion that lies outside of the boundary.
- Yes: Any features that cross the search envelope boundary will be clipped at the boundary, and only the portion that lies inside the boundary will be read. The underlying function for the Clip to Search Envelope function is an intersection; however, when Clip to Search Envelope is set to Yes, a clip is also performed in addition to the intersection.
Use Network Authentication
This parameter is always visible in some formats, and visible in other formats only when the dataset is a URL.
Specify the authentication method to use when accessing a password-protected server.
- Basic: (default) Basic access authentication is designed to allow a client to provide credentials to a server on the assumption that the connection between them is trusted and secure. Note that any credentials passed from client to server can be easily intercepted through an insecure connection.
- Digest: Digest authentication is one of the agreed-upon methods a web server can use to negotiate credentials, such as username or password, with a user's web browser.
- NTLM: A challenge-response protocol that is used to provide compatibility with versions of Windows earlier than the Windows 2000 operating systems.
- Web Connection: Web connections provide a convenient and secure way to store and reuse previously established connection parameters. See Web Connection below.
- Single Sign-on: FME will use the credentials of the current user to authenticate the HTTP request. This authentication method currently works only on the Windows operating system.
Note: To access datasets using a proxy server, use the Network tools in FME Options. From the Workbench menu, select Tools > FME Options > Network. For more information, see "Network Proxy" in the FME Workbench Help.