FME Flow: 2025.2
Proxy
Select System Configuration > Network & Email tab.
- Estimated Time Required: 15-20 minutes
- Skill Level: Intermediate
- Prerequisites:
- Proxy server address is known.
A proxy server is a computer on your LAN that allows you to connect to external servers without compromising the security of your internal network. If you are consuming FME Flow Web Services and your organization uses a proxy server on your network, you can configure FME Flow to connect through the proxy.
What is not supported on a proxy in FME Flow?
- Certain Database Connections, including connections to MongoDB databases, will fail. Safe Software has not fully tested proxy support for all database formats; you may need to test your database connections to determine support.
- If Authentication Method Digest or NTLM is specified in the configuration settings below, these connections will fail:
- Connections to Azure Active Directory for user authentication with FME Flow.
- Web Connections
- Automations external actions that Email, or the Notification Service Email Subscriber.
- Automations external actions that notify an Azure Event Grid Topic, or the Notification Service Azure Event Grid Subscriber.
- Automations or Notification Service tools that connect to Dropbox, including the Dropbox Directory trigger, Dropbox Directory external action, Dropbox Watch Publisher, and Dropbox Subscriber.
- Automations or Notification Service protocols (including triggers, external actions, publishers, and subscribers) that do not communicate through HTTP. These protocols include watching directories, email (SMTP and IMAP), FTP, JMS, SFTP, UDP, and WebSocket.
- (Windows) Any applicable Exceptions configured in your Proxy server LAN Settings (under Internet Properties) or in a PAC file.
- (Linux) Any applicable exceptions configured in network tools or the /etc/environment file.
Can I map URLs through a custom proxy?
Custom proxy maps must be configured manually. For more information, see To Configure Custom Proxy Maps (Manual) (below).
To Configure FME Flow with a Proxy Server
Click Proxy. Complete the following fields, and click Save.
- Proxy Enabled: Click to enable a proxy connection.
- Host: The proxy server hostname.
- Port: The port through which communication with the proxy server takes place.
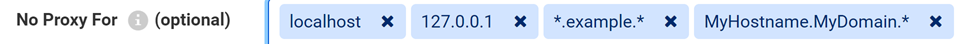
- No Proxy For: (optional) A list of hostnames and IP addresses that will be accessed through a direct connection, bypassing the proxy. To avoid entering multiple hosts in the same domain, hosts can be prefixed and appended with the wildcard character *.
- Authentication Required: Click if authentication is required to access the proxy server.
- Username: The account username for running the proxy server.
- Password: The password for the proxy server account.
- Authentication Method: The authentication method used by the proxy server, either Basic, Digest, or NTLM.
To delimit the list, use commas, semicolons, or press the tab or enter keys. Do not copy-paste a list of entries. To delineate properly in the display, each entry must be added separately.
Example:
To Configure Custom Proxy Maps (Manual)
You can specify custom proxy maps instead of using the system proxy. A custom proxy map allows you to map access to specific URLs through an alternative proxy on your system. Use a custom proxy map if you need to bypass your network's default rules or system proxy settings in order to access these URLs.
When configuring custom proxy maps, keep in mind the following:
- Unlike a system proxy, custom proxies apply only to connections from FME Engines. Connections from the FME Flow Core, such as accessing Resources, Database Connections and Web Connections, and Automations trigger and external action notifications, are not supported through custom proxies.
- Custom proxy maps do not work in conjunction with configuring FME Flow with a system proxy (described above, under To Configure FME Flow with a Proxy Server). You can configure only one or the other.
- Run the Windows Command Prompt as administrator, and navigate to: $(FME_SERVER_HOME)\Server\fme
- Run the following command, repeating all parameters for each URL you want to map through the custom proxy, as shown:
- <Source_URL> is the URL you want to access. The URL must be an exact match with the URL in the request; for example, http://www.lib.uwaterloo.ca/locations/umd/digitization_project/Roads_NTDB.zip.
- <Proxy_URL> is the URL of the proxy server on your system that will handle requests to the <Source_URL>.
- <Proxy_Port> is the port number on the proxy server through which requests are handled.
- <Requires_Authentication> is true or false, depending on whether the proxy server requires authentication to access. If true, provide <UserName>, <Password>, and <Authentication_Method> (Basic, Digest, or NTLM).
- Open fmeFlowConfig.txt.
- Under the heading FME SERVER SETTINGS START, add the following line:
- Save and close the file.
- Restart FME Flow.
fme.exe APPLY_SETTINGS SYSTEM "Proxy/Custom Proxy Map" "<Source_URL>,<Proxy_URL>,<Proxy_Port>,<Requires_Authentication>,<UserName>,fme_encrypt(<Password>),<Authentication_Method>[,<Source_URL>,<Proxy_URL>,<Proxy_Port>,<Requires_Authentication>,<UserName>,fme_encrypt(<Password>),<Authentication_Method>]"
Where:
ENABLE_ENGINEPROXY=false
Other Notes
To use a proxy server without authentication, instead specify:
fme.exe APPLY_SETTINGS SYSTEM "Proxy/Proxy Server Require Authentication" "false"
To stop using the proxy server, run:
fme.exe APPLY_SETTINGS SYSTEM "Proxy/Proxy Setting" "No Proxy"
- Run the Linux command line and navigate to: /opt/fme-engine-<year>, where <year> is the FME Flow release version, such as 2016.
- For each URL you want to map through the custom proxy, run the following command:
- <Source_URL> is the URL you want to access. The URL must be an exact match with the URL in the request; for example, http://www.lib.uwaterloo.ca/locations/umd/digitization_project/Roads_NTDB.zip.
- <Proxy_URL> is the URL of the proxy server on your system that will handle requests to the <Source_URL>.
- <Proxy_Port> is the port number on the proxy server through which requests are handled.
- <Requires_Authentication> is true or false, depending on whether the proxy server requires authentication to access. If true, provide <UserName>, <Password>, and <Authentication_Method> (Basic, Digest, or NTLM).
- Open fmeFlowConfig.txt.
- Under the heading FME SERVER SETTINGS START, add the following line:
- Save and close the file.
- Restart FME Flow.
./fme APPLY_SETTINGS SYSTEM "Proxy/Custom Proxy Map" "<Source_URL>,<Proxy_URL>,<Proxy_Port>,<Requires_Authentication>,<UserName>,<Password>,<Authentication_Method>"
Where:
ENABLE_ENGINEPROXY=false
Other Notes
To use a proxy server without authentication, instead specify:
./fme APPLY_SETTINGS SYSTEM "Proxy/Proxy Server Require Authentication" "false"
To stop using the proxy server, run:
./fme APPLY_SETTINGS SYSTEM "Proxy/Proxy Setting" "No Proxy"