| Database Connections |
|---|
|
Connections store authentication information. For general information about sharing database connections, please see Using Database Connections. Note that different subsets of Database Connection parameters are made available in different contexts. Select an existing connection, or Add Database Connection to define a new connection. The new connection can be made visible only to the current user, or can be shared among multiple users. |
Connection Parameters
The host name of the Microsoft SQL Server or Azure SQL database. (It is not necessary to specify a port if a default configuration is used.)
If you have configured your Microsoft SQL Server database to use a non-standard port number, you can specify this port here.
The correct syntax is:
<Host Name or IP>,<port>
The name of the database to connect to.
- Windows Authentication: Select this option when connecting through a Windows user account, and the database can validate the account name and password using the Windows principal token in the operating system. Since the user account is retrieved by Windows, the Username and Password parameters are ignored.
- SQL Server Authentication: Select this option to proceed with specifying login credentials through the Username and Password parameters.
Enter the username and password to access the database, user account, or wherever authentication is required.
Note: Note: This parameter is not present in the Azure SQL Database reader and writer. The Azure SQL Database reader and writer will always request Secure Sockets Layer (SSL) encrypted connections.
When selected, this parameter requests Secure Sockets Layer (SSL) encryption for the connection. If the server does not have a certificate trusted by the client machine, the connection will fail. Otherwise, data will be encrypted before traveling over the network. There are multiple ways to trust a server certificate on a client machine.
If this parameter is not selected, encryption behavior will be determined by encryption properties set for SQL Server Native Client, and for SQL Server.
Note: Tip: When Encrypt Connection is selected, please provide a fully qualified Server name. For example, a server named safe-sql-server might have a fully qualified name of safe-sql-server.dev.safe. This fully qualified name should be an exact match for the server name on the trusted certificate.
The time, in seconds, after which to terminate a query to the database if it has not yet returned a result.
If set to 0, there is no timeout. The default is 30.
Note: If this value is not set high enough, then the query will return the error Provider Error - Timeout Expired.
Constraints
Enter (or browse for) the name(s) of specific database table(s) to extract.
This optional specification is used to limit the rows read by the reader from each table. This example selects only the features whose lengths are more than 2000:
LENGTH > 2000
Schema Attributes
Use this parameter to expose Format Attributes in Workbench when you create a workspace:
- In a dynamic scenario, it means these attributes can be passed to the output dataset at runtime.
- In a non-dynamic scenario where you have multiple feature types, it is convenient to expose additional attributes using this one parameter. For example, if you have ten feature types and want to expose the same attribute in each one, it is easier to define it once than it is to set each feature type individually in the workspace.
Using the minimum and maximum x and y parameters, define a bounding box that will be used to filter the input features. Only features that intersect with the bounding box are returned.
If all four coordinates of the search envelope are specified as 0, the search envelope will be disabled.
When selected, this parameter removes any portions of imported features being read that are outside the Search Envelope.
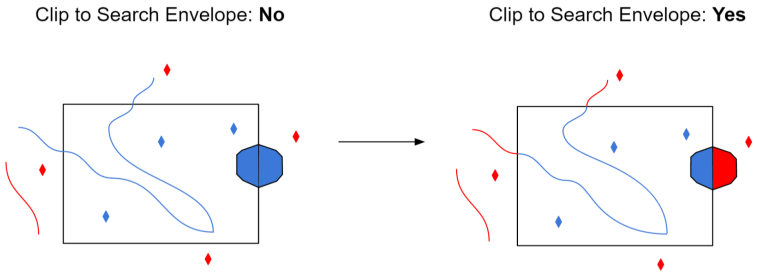
The example below illustrates the results of the Search Envelope when Clip to Search Envelope is not selected (set to No) and when it is selected (set to Yes).
- No: Any features that cross the search envelope boundary will be read, including the portion that lies outside of the boundary.
- Yes: Any features that cross the search envelope boundary will be clipped at the boundary, and only the portion that lies inside the boundary will be read. The underlying function for the Clip to Search Envelope function is an intersection; however, when Clip to Search Envelope is selected, a clipping operation is also performed in addition to the intersection.